What is Centinela
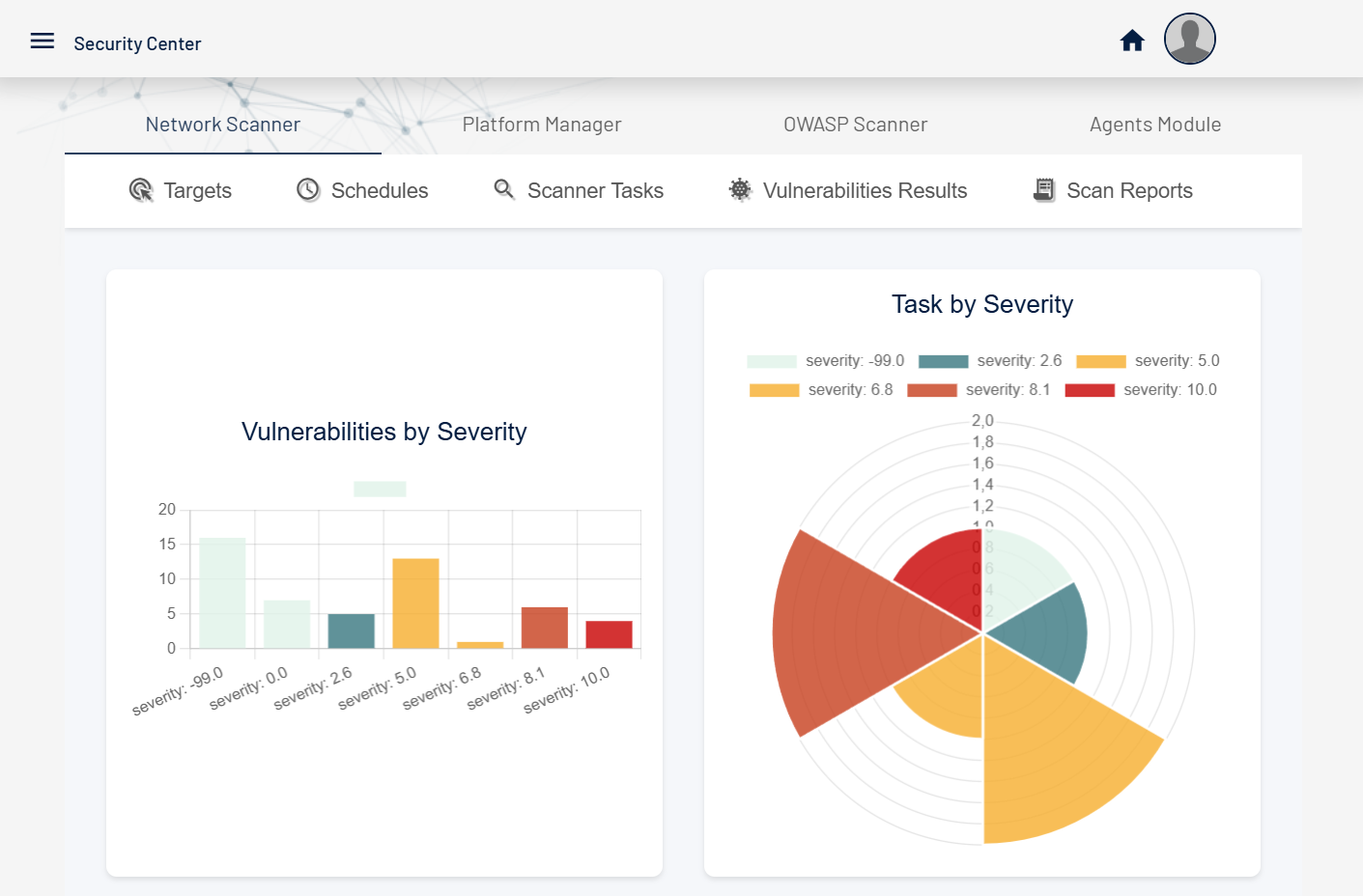
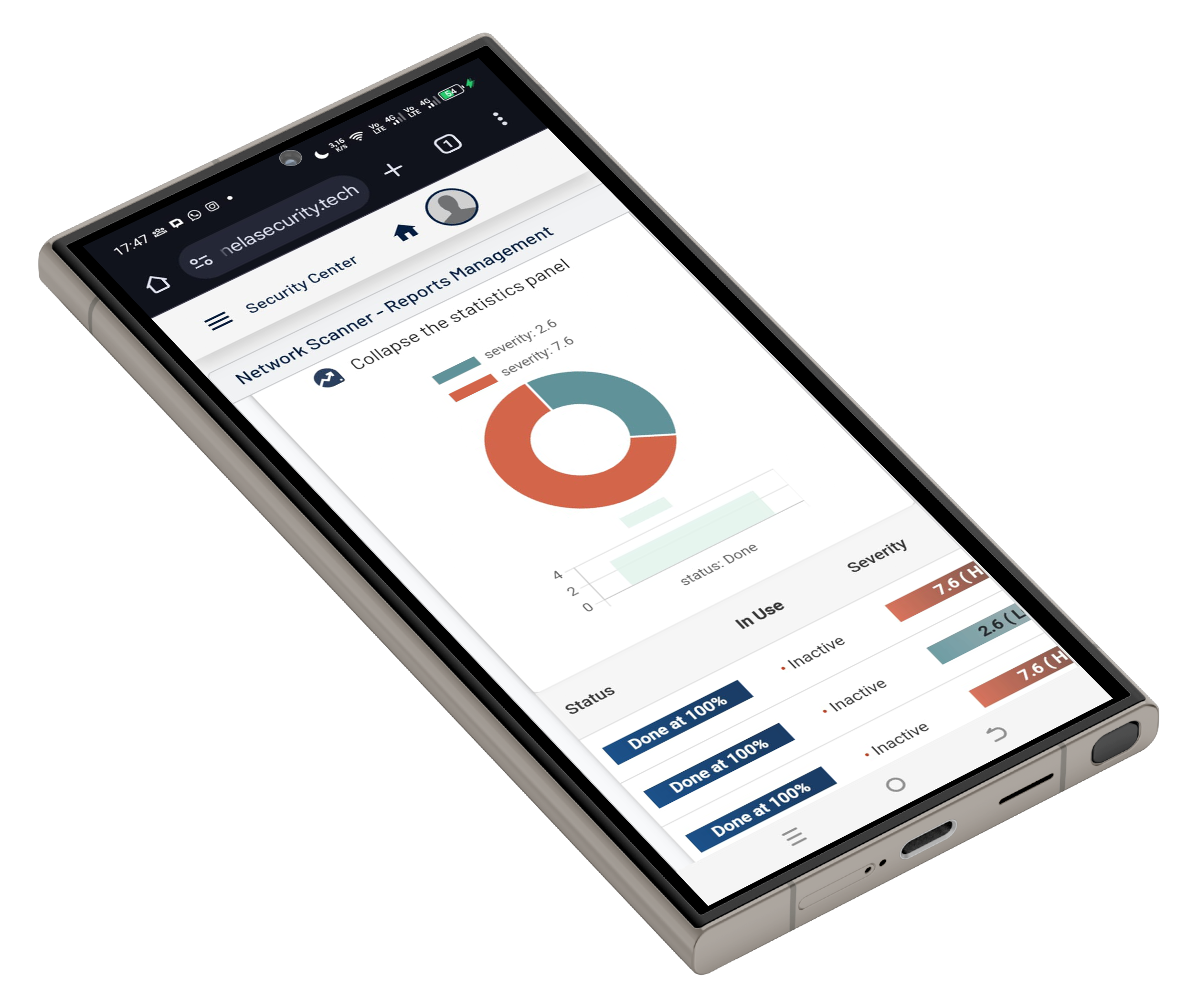
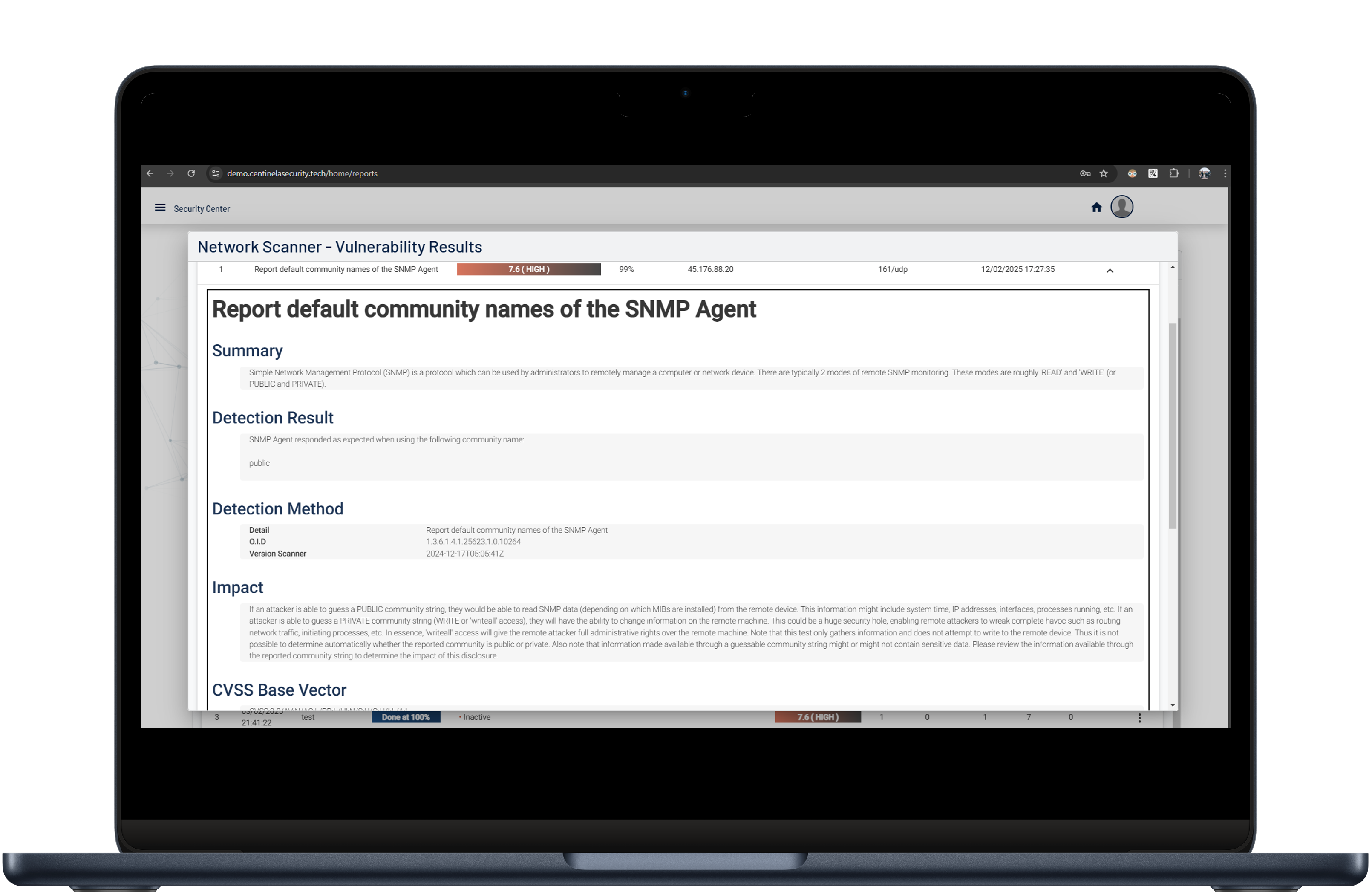
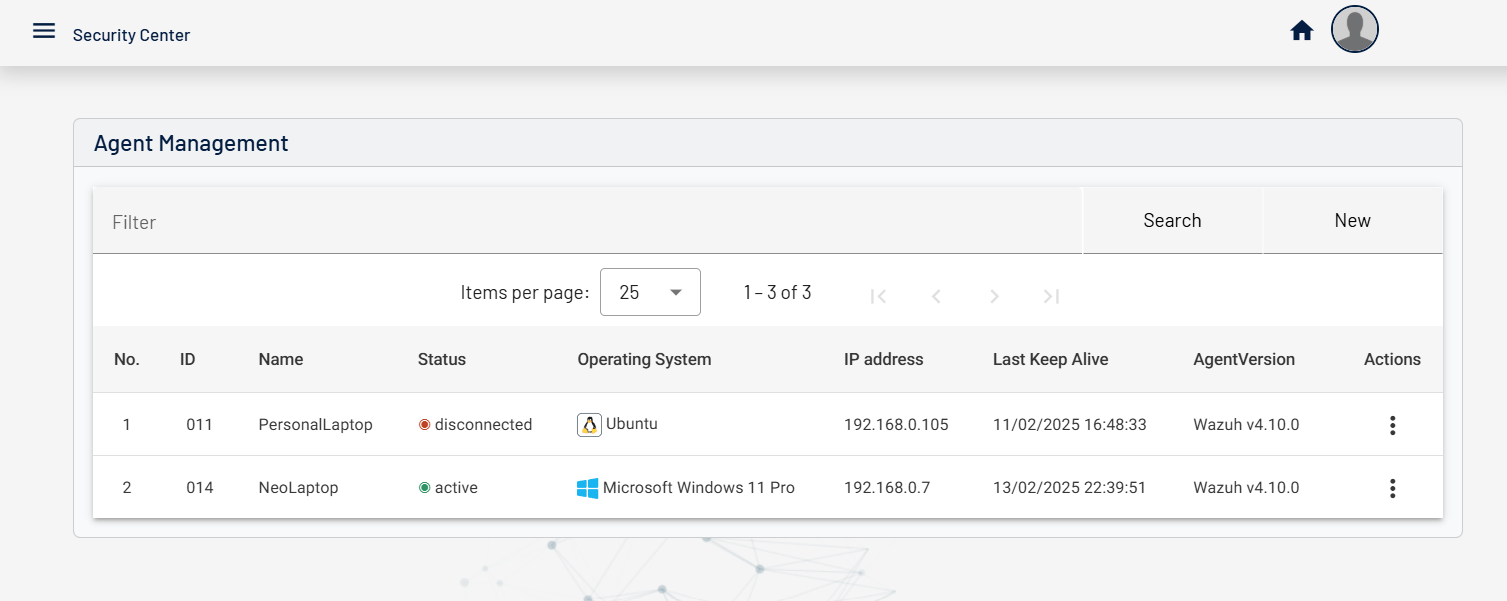
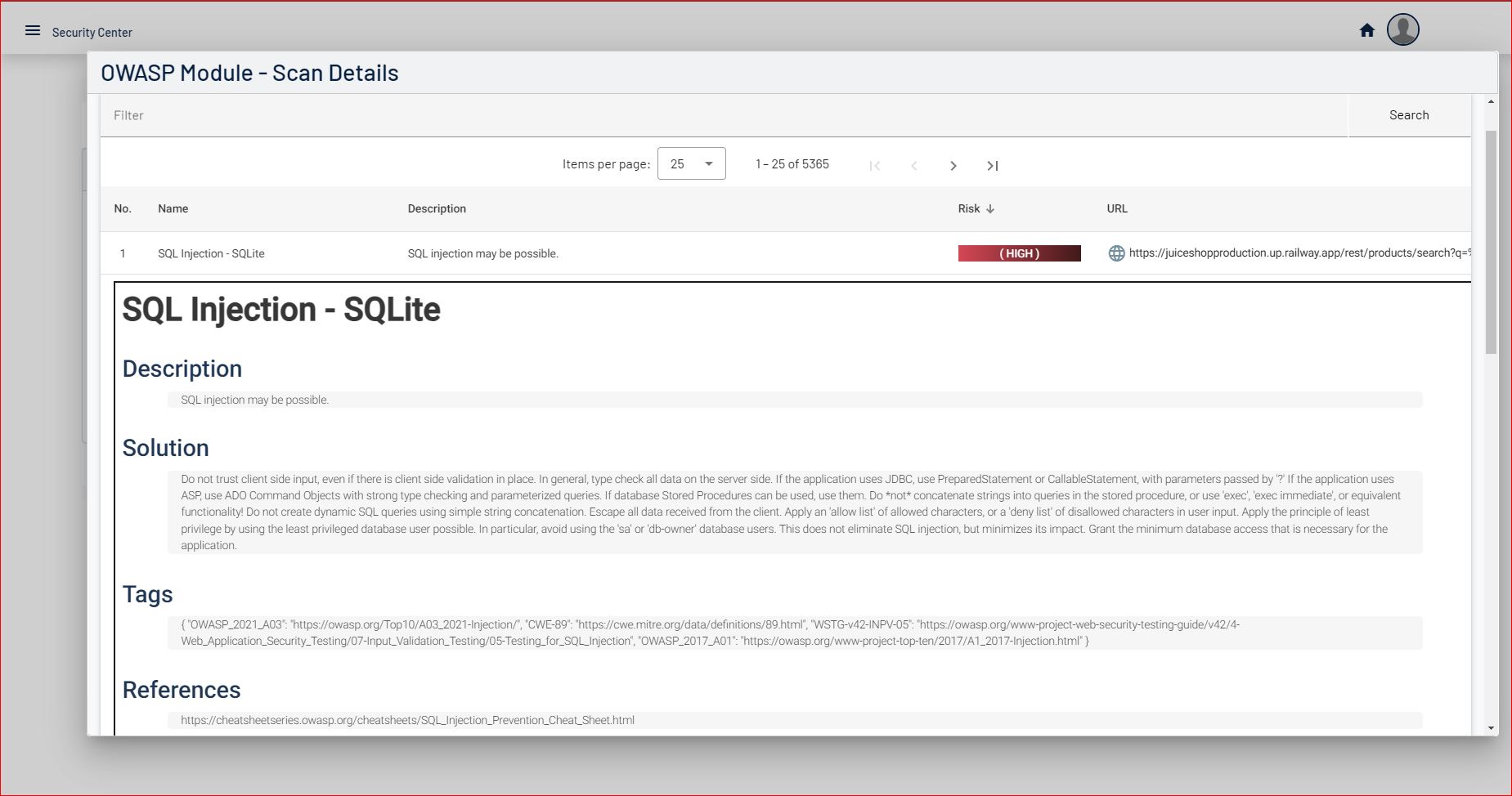
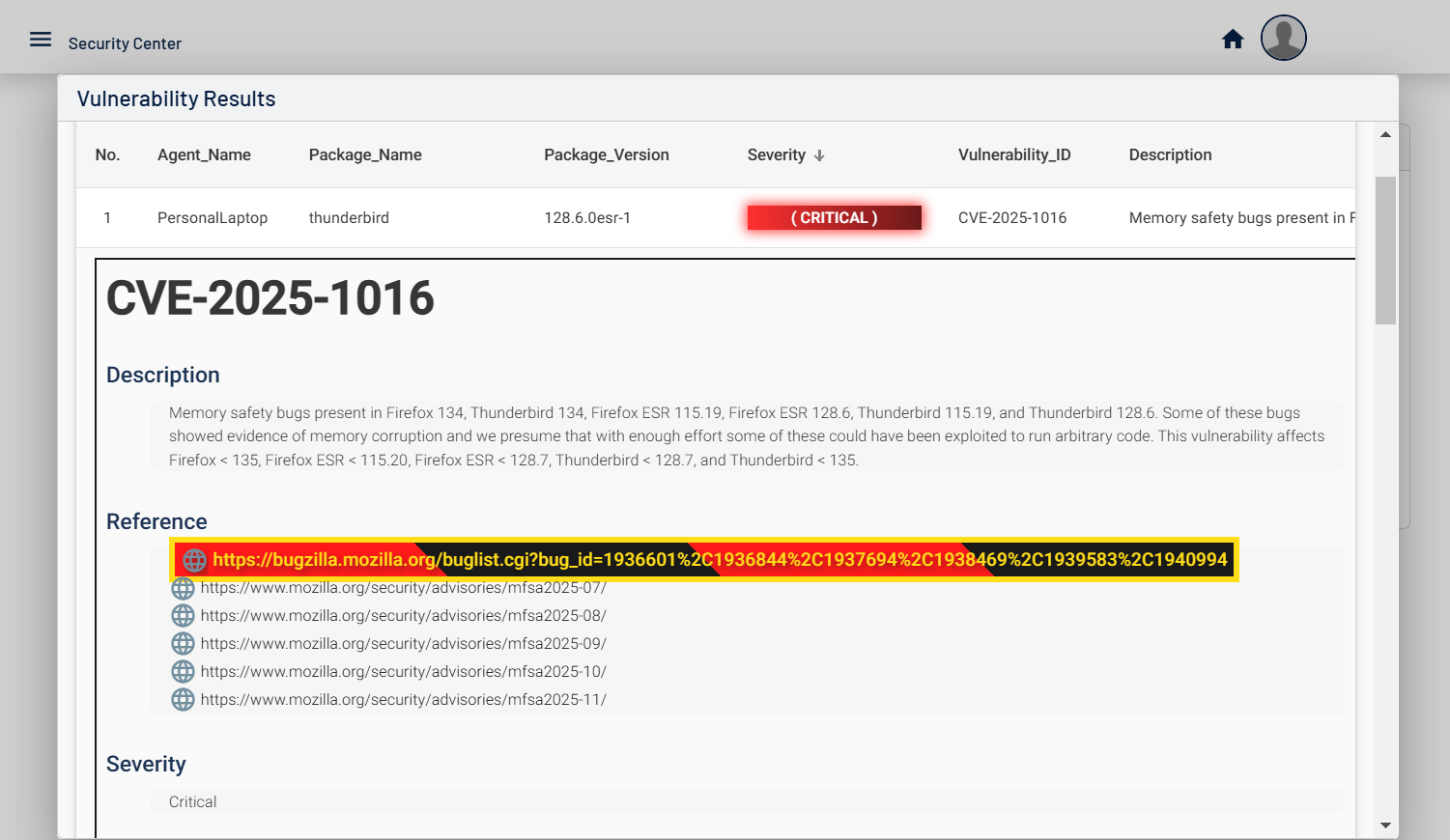
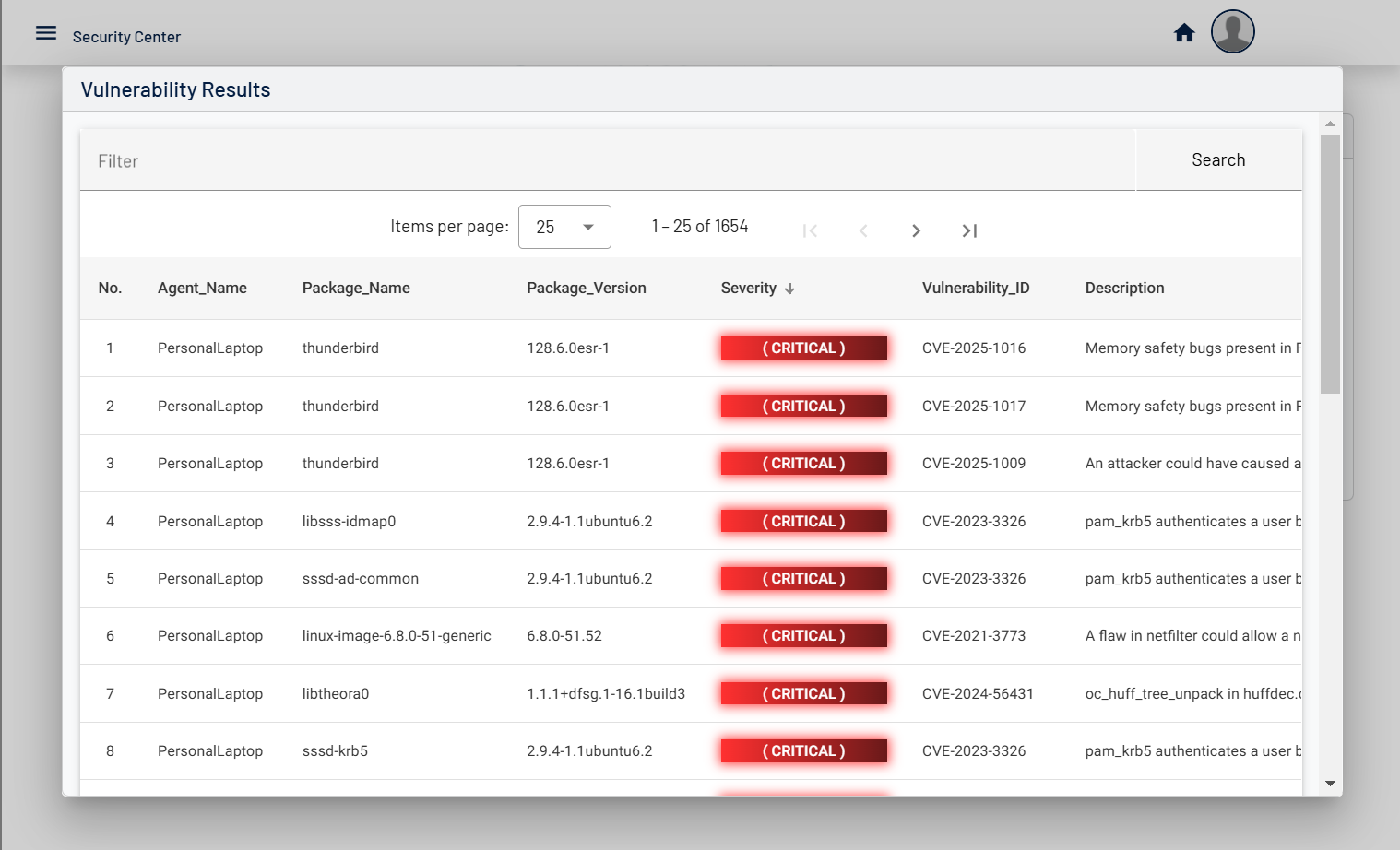
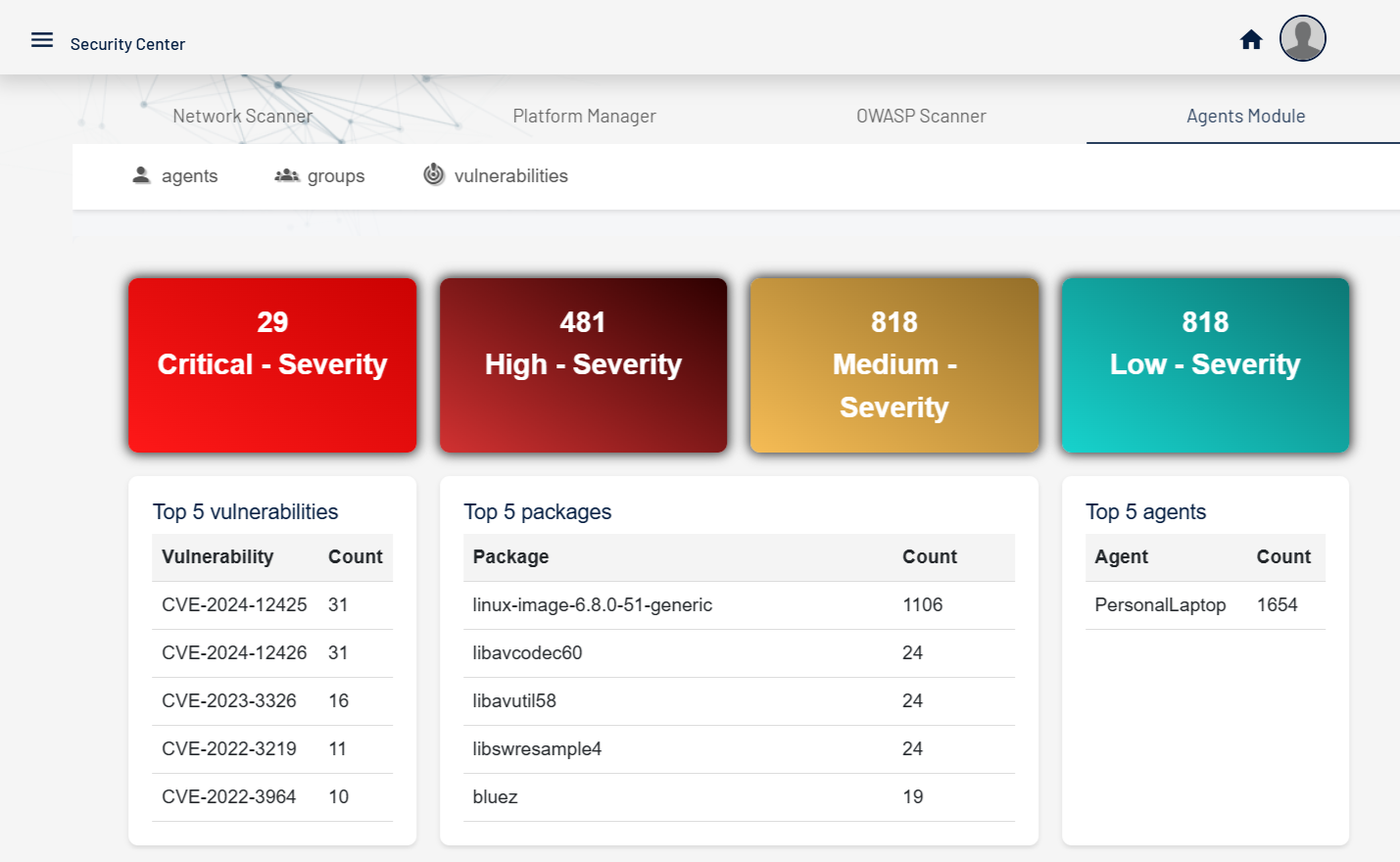
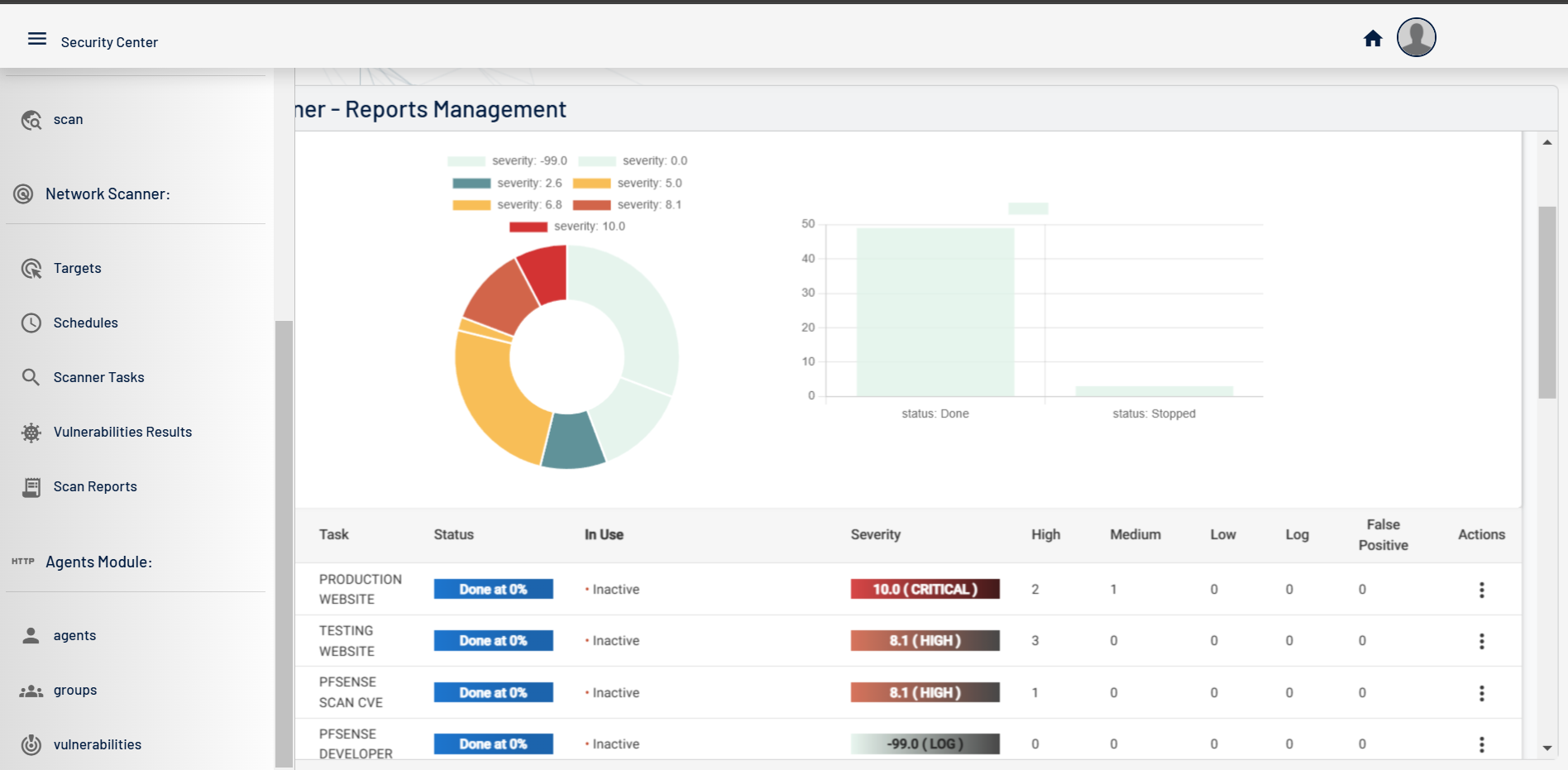
Centinela is an advanced vulnerability management platform that helps businesses secure their infrastructure.
Designed for efficiency, Centinela provides insights, detailed reports, and proactive threat detection to keep your systems protected.